By Rajesh Shukla
Sample Paper 1 Solution Sample Paper 1
Sample Paper 2 Solution Sample Paper 2
Class XII
Sample paper : 1( Solutions)
Subject : Python
Max. Marks: 70 Time : 3 hrs
General Instructions:
- All questions are compulsory.
- Question paper is divided into 4 sections A, B, C and D.
- Section A : Unit-1 [30 marks (Q1,Q2,Q3)]
- Section B : Unit-2 [15 marks(Q4)]
- Section C: Unit-3 [15 marks(Q5)]
- Section D: Unit-4 [10 marks(Q6)]
Section A
Q1.
a.
Sol: (iv) and
(it is not an arithmetic operator rather it is relational operator)
b.
Sol:
Keyword: Keyword is a special word that has a special meaning and purpose. Keywords are reserved and should not be used as variable/identifiers.
Example of keywords are : if, elif, else, etc.
Identifiers: Identifiers are user-defined names given to a part of a program like: variable, object, functions etc. identifiers are not reserved. These are defined by the user and consist of letters, digits and a symbol underscore (_). They must begin with either a letter or an underscore character.
Example:abc, roll,name,_abc etc.
c.
Sol:
(i) floor() : import math
(ii) sin() : import math
d.
Sol:
def sum(n1,n2):
s=n1+n2
print("Sum = ",s)
function calling
a=int(input("Enter 1st no "))
b=int(input("Enter 2nd no "))
sum(a,b)
e.
Sol:
Output:hell123o
Q2.
a
#function definition
def show(n):
for i in n:
print(i,iii)
#function calling
list1=[3,2,5,4,10]
show(list1)
b.
Sol: (iv) tuple
c.
STACKS IN PYTHON
A stack is an ordered collection of elements into which items/elements may be added or deleted at one end called the top of the stack. i.e. whenever an element is added it will be added at the top of the stack and whenever an element is deleted it will be deleted from the top of the stack.
Stack follows the policy of LIFO (last in first out) i.e. the element which is added at the end will be the first to be deleted.
Operations
(i). PUSH (addition of element):
Whenever an element is added in the stack it is always added at the top of the stack. And the newly added node becomes the top of the stack.
(ii). POP (Deletion of element)
Whenever an element is deleted from the stack it is always deleted from top of the stack and after its deletion the next node in sequence becomes the top of the stack.
APPLICATIONS OF STACKS
Some of the important applications of stacks include:
Reversing a word / line
A simple example of stack application is reversal of a given line. This can be accomplished by pushing each character on to a stack as it is read. When the line is finished , characters are then popped off the stack and they will come off in the reverse order.
Recursion
The compiler uses stack to store the previous state of a program when a function is called or during recursion.
Syntax Parsing
Many compilers use a stack for parsing the syntax of expressions, program blocks etc. before translating into low level code.
Backtracking
Another important application is backtracking (backtracking is a form of recursion, but it involves choosing only one option out of the possibilities.)
Backtracking is used in large number of puzzles like Sudoku and in optimization problem such as knapsack.
Parenthesis Checking
Stack is used to check the proper opening and closing of parenthesis.
Undo mechanism
Undo mechanism in text editors: this operation is accomplished by keeping all the text changes in a stack.
Browser
Browser also uses stack to store the sites visited by the user. On clicking back button we are taken to previous sites visited.
Expression Evaluation
Stack is used to evaluate prefix, postfix and infix expressions.
Expression Conversion
An expression can be represented in prefix, postfix or infix notation. Stack can be used to convert one form of expression to another.
String Reversal
Stack is used to reverse a string. We push the characters of string one by one into stack and then pop character from stack.
Function Call
Stack is used to keep information about the active functions or subroutines.
d.
(Maintaing Book details like bcode,btitle and price using stacks)
"""
push
pop
traverse
"""
book=[]
def push():
bcode=input("Enter bcode ")
btitle=input("Enter btitle ")
price=input("Enter price ")
bk=(bcode,btitle,price)
book.append(bk)
def pop():
if(book==[]):
print("Underflow / Book Stack in empty")
else:
bcode,btitle,price=book.pop()
print("poped element is ")
print("bcode ",bcode," btitle ",btitle," price ",price)
def traverse():
if not (book==[]):
n=len(book)
for i in range(n-1,-1,-1):
print(book[i])
else:
print("Empty , No book to display")
while True:
print("1. Push")
print("2. Pop")
print("3. Traversal")
print("4. Exit")
ch=int(input("Enter your choice "))
if(ch==1):
push()
elif(ch==2):
pop()
elif(ch==3):
traverse()
elif(ch==4):
print("End")
break
else:
print("Invalid choice")
Q3.
a.
Sol:
QUEUES IN PYTHON
Queue is an ordered collection of elements/items from which elements may be deleted from one end called the “FRONT” of the queue and into which the elements may be inserted from another end called the “REAR” of the queue.
Queue follows the policy of FIFO ( First in first out) i.e. the element which is added first will be the first to be deleted/processed.
Operations
(i). Addition of element
Whenever an element is added in the queue it is always added from the rear of the queue, and after addition of element the newly added node becomes the rear of the queue.
(ii). Deletion of element
Whenever an element is deleted from the queue it is always deleted from the front of the queue, and after its deletion the next node in sequence becomes the front of the queue.
b.
Sol: count and print total lower case alphabets in the file
#count and print total lower case alphabets in the file
def count_lower():
lo=0
with open("story.txt") as f:
while True:
c=f.read(1)
if not c:
break
print(c,end='')
if(c>='a' and c<='z'):
lo=lo+1
print("total lower case alphabets ",lo)
#function calling
count_lower()
or
to count the number of words in a text file “story.txt” which are starting with alphabet ‘D’ or ‘d’ .
def count_words():
w=0
with open("story.txt") as f:
for line in f:
for word in line.split():
if(word[0]=="d" or word[0]=="D"):
print(word)
w=w+1
print("total words starting with 'a' are ",w)
#function calling
count_words()
c.
Sol: factorial of number
def fact(n):
f=1
i=1
while(i<=n):
f=f*i
i=i+1
print("Factorial = ",f)
#function calling
a=int(input("Enter any no "))
fact(a)
Section B
Q.4.
a.
Sol:
(i). DNS : Domain Name System
(ii). TCP/IP : Transmission control protocol / internet protocol
(iii). WAN : Wide area network
(iv). FTP : File transfer protocol
b.
Sol: difference between LAN and WAN
| LAN | WAN | |
| Stands for | Local Area Network | Wide Area Network |
| Covers | Local areas only (e.g., homes, offices, schools) | Large geographic areas (e.g., cities, states, nations) |
| Definition | LAN (Local Area Network) is a computer network covering a small geographic area, like a home, office, school, or group of buildings. | WAN (Wide Area Network) is a computer network that covers a broad area (e.g., any network whose communications links cross metropolitan, regional, or national boundaries over a long distance). |
| Speed | High speed (1000 mbps) | Less speed (150 mbps) |
| Data transfer rates | LANs have a high data transfer rate. | WANs have a lower data transfer rate compared to LANs. |
| Example | The network in an office building can be a LAN | The Internet is a good example of a WAN |
| Data Transmission Error | Experiences fewer data transmission errors | Experiences more data transmission errors as compared to LAN |
| Ownership | Typically owned, controlled, and managed by a single person or organization. | WANs (like the Internet) are not owned by any one organization but rather exist under collective or distributed ownership and management over long distances. |
c.
Sol:
Define the following:
(i). Repeater (ii). Router
Sol:
Repeater: A repeater is a device that regenerates the received signals and retransmits to its destination, since signal becomes weak after a certain distance and cannot reach its destination. So regeneration of signals required. In such case a Repeater is used.
Router: A router is hardware device designed to receive, analyze and move incoming packets to another network. It may also be used to convert the packets to another network interface, drop them, and perform other actions relating to a network.
d.
Sol:one advantage and one disadvantage of optical fibre.
Advantage :
It is free from electrical noise and interference.
Disadvantage :
it is an expensive communicable medium.
e.
Sol: what is cloud computing
cloud computing is the delivery of computing services—including servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale. You typically pay only for cloud services you use, helping lower your operating costs, run your infrastructure more efficiently and scale as your business needs change.
f.
Sol:
(i).
(Any of the following option)
Layout Option 1
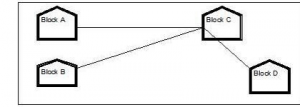
Layout Option 2
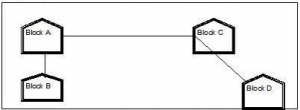
(ii)
The most suitable place / block to house the server of this organization would be Block C, as this block contains the maximum number of computers, thus decreasing the cabling cost for most of the computers as well as increasing the efficiency of the maximum computers in the network.
(iii)
For Layout 1, since the cabling distance between Blocks A and C, and that between B and C are quite large, so a repeater each would ideally be needed along their path to avoid loss of signals during the course of data flow in these routes.
For layout 2, since the distance between Blocks A and C is large so a repeater would ideally be placed in between this path.
In both the layouts, a hub/switch each would be needed in all the blocks, to
Interconnect the group of cables from the different computers in each block.
(iv)
The most economic way to connect it with a reasonable high speed would be to use radio wave transmission, as they are easy to install, can travel long distances, and penetrate buildings easily, so they are widely used for communication, both indoors and outdoors. Radio waves also have the advantage of being omni directional, which is they can travel in all the directions from the source, so that the transmitter and receiver do not have to be carefully aligned physically.
SECTION-C
Q.5.
a.Which command is used to display the structure of the table?
Sol: Desc / Describe
b. Which clause is used to sort the records of a table?
Sol: Order by
c. Which command is used to remove the records of the table?
Sol: delete
d. Which clause is used to remove the duplicating rows of the table?
Sol: distinct
e.
Sol:
Primary key
A primary key, also called a primary keyword, is a key in a relational database that is unique for each record. It is a unique identifier, such as a driver license number, telephone number (including area code), or vehicle identification number (VIN). A relational database must always have one and only one primary key. Primary keys typically appear as columns in relational database tables.
Candidate key
A candidate key is a column, or set of columns, in a table that can uniquely identify any database record without referring to any other data. Each table may have one or more candidate keys, but one candidate key is unique, and it is called the primary key. This is usually the best among the candidate keys to use for identification.
When a key is composed of more than one column, it is known as a composite key.
f
Sol:
(i) To display GCODE and DESCRIPTION of each GARMENT in descending order of GCODE.
Sol:
SELECT GCODE DESCRIPTION FROM GARMENT ORDER BY GCODE DESC;
(ii) To display the average PRICE of all the GARMENTs, which are made up of FABRIC with FCODE as F03.
Sol:
SELCECT AVG(PRICE) FROM GARMENT WHERE GARMENT.FCODE=’F03’;
(iii) To display FABRIC with highest and lowest price of GARMENTS from GARMENT table.
Sol:
SELECT FCODE, MAX(PRICE), MIN(PRICE) FROM GARMENT GROUP BY FCODE;
(iv)SELECT SUM(PRICE) FROM GARMENT WHERE FCODE=’F01’;
Sol:
2600
(v)SELECT COUNT(DISTINCT PRICE) FROM GARMENT;
Sol:
7
g.
Sol:
(i). sum()
the sum function returns the total sum of a numeric column. it gives the sum total of all the values present in a particular column. NULLl values in the column are ignored.
example:
total salary amount distributed to employee of a company.
select sum(sal) from employee;
total salary amount distributed to all managers of a company.
select sum(sal) from employee where desig=’manager’;
(ii). Count()
count() function is used to count the number of non null values in a column. count() function take one argument i.e. name of the column.
to count total number of employee.
select count(*) from employee;
(iii). Max()
The max() function returns the largest / highest value amoung the given set of values of a any column. name of the column is given as an agument. NULL values in the column are ignored.
select max(sal) from employee;
seelct max(sal) from where desig=’manager’;
(iv). Avg()
avg() function helps us to find the average value of any column or expresion based on a column. It accepts one argument i.e. name of the column whose average value has to be calculated. NULL values in the column are ignored.
example:
Average salary amount distributed to employee of a company.
select avg(sal) from employee;
average salary amount distributed to all managers of a company.
select avg(sal) from employee where desig=’manager’;
SECTION-D
Q.6
Sol:
a. It is an internet service for sending written messages electronically from one computer to another. Write the service name.
Sol:
email
b. What can be done to reduce the risk of identity theft? Write any two ways.
Sol:
Identity theft refers to the theft of personal data of the victim and using it for some illegal purposes. it is the most common types of fraud that may lead to financial lossesand at times may result in cirminal actions.
A few steps to follow in order to prevent identity thefts are:
ensure a strong and unique password
do not post personal information on social media
show from known and trusted websites only
c. What do you understand by “privacy of data”?
Sol:
The ethical and legal rights that individuals have with regards to the control over discussions and use of their personal information is known as privacy of data.
d. Name the crimes for which cyber laws are enforced strictly in India?
Sol:
cybercrimes
electronic and digital signature
intellectual property
data protection and privacy
e. If someone hacks your website, who would you complain to?
Sol:
The complaint has to be lodged to the police under the IT Act.
f. What are the different ways in which authentication of a person can be performed?[2]
Sol:
Different methods of user identifications and authentication are:
password: this is somthing the user should know from the time they start the activity.
otp: A one time pin or password is sent to the user to verify their identity.
biometrics: this means biological characteristics of a person registered for verification.
By Rajesh Shukla
Sample Paper 1 Solution Sample Paper 1
Sample Paper 2 Solution Sample Paper 2
CBSE Class 12 @ Python
Tutorials | Technical Questions | Interview Questions |
|---|---|---|
|
C Programming C++ Programming Class 11 (Python) Class 12 (Python) |
C Language C++ Programming Python |
C Interview Questions C++ Interview Questions C Programs C++ Programs |




