By Rajesh Shukla
Sample Paper 1 Solution Sample Paper 1
Sample Paper 2 Solution Sample Paper 2
Class XII
Sample paper : 2(Solutions)
Subject : Python
Max. Marks: 70 Time : 3 hrs
General Instructions:
- All questions are compulsory.
- Question paper is divided into 4 sections A, B, C and D.
- Section A : Unit-1 [30 marks (Q1,Q2,Q3)]
- Section B : Unit-2 [15 marks(Q4)]
- Section C: Unit-3 [15 marks(Q5,Q6)]
- Section D: Unit-4 [10 marks(Q7)]
Section A
Q.1
a.
Sol:
(iii) ^
c.
Sol:
(i) floor() : import math
(ii) sin() : import random
d.
Sol:
def square(n):
s=n*n
print("square = ",s)
def cube(n):
c=nnn
print("Cube = ",c)
#function calling
a=10
print("Number ",a);
square(a)
a=5
print("Number ",a)
cube(a)
e.
Sol:
Output: hEllObbbbbbhI
Q2.
a
Sol.
#function definition
def show(n):
for i in n:
if(i%2==0):
s=ii else: s=ii*i
print(i," : ",s)
#function calling
list1=[4,3,6,5,10,2]
show(list1)
b.
Sol:
(i) list
c.
Sol:
3 times
d.
Sol:
Sol:d. sine chart
Q3.
a.
Sol:
#queue implementation (using functions)
#program to create a queue of employee(empno,name,sal).
"""
add employee
delete employee
traverse / display all employees
"""
employee=[]
def add_element():
empno=input("Enter empno ")
name=input("Enter name ")
sal=input("Enter sal ")
emp=(empno,name,sal)
employee.append(emp)
def del_element():
if(employee==[]):
print("Underflow / Employee Stack in empty")
else:
empno,name,sal=employee.pop(0)
print("poped element is ")
print("empno ",empno," name ",name," salary ",sal)
def traverse():
if not (employee==[]):
n=len(employee)
for i in range(0,n):
print(employee[i])
else:
print("Empty , No employee to display")
while True:
print("1. Add element");
print("2. Delete element");
print("3. Traversal")
print("4. Exit")
ch=int(input("Enter your choice "))
if(ch==1):
add_element()
elif(ch==2):
del_element();
elif(ch==3):
traverse()
elif(ch==4):
print("End")
break
else:
print("Invalid choice")#function definition
b.
Sol:
def count_vowels():
d=0
vowels="aeiouAEIOU"
with open("story.txt") as f:
while True:
c=f.read(1)
if not c:
break
print(c,end='')
if(c in vowels):
d=d+1
print("total digits ",d)
#function calling
count_vowels()
c.
Sol:
def table(n):
i=1
t=0
while(i<=10):
t=n*i
print(t)
i=i+1
#function calling
a=int(input("Enter any no "))
table(a)
Section B
a.
Sol:
(i). HTTP : Hyper Text Transfer Protpcol
(ii). FTP : File transfer protocol
(iii). PPP : Point to point protocol
(iv). POP : Post Office protocol
b.
Sol:
Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. The term is generally used to describe data centers available to many users over the Internet.
Fig:
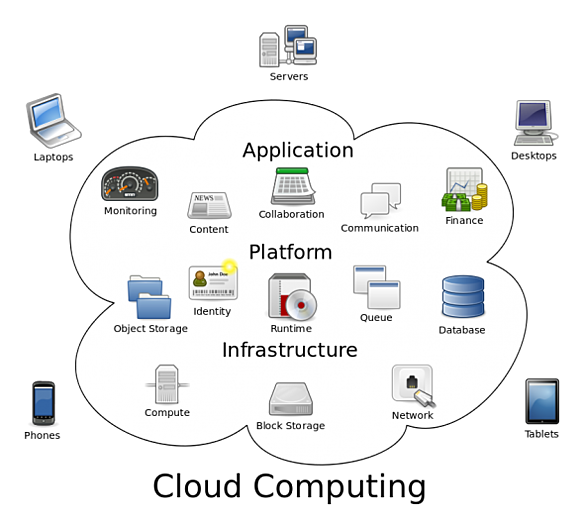
Cloud computing benefits
Efficiency / cost reduction.
Data security.
Scalability.
Mobility.
Disaster recovery.
Control.
Competitive edge.
c.
Sol:
Bridges:
A bridge is a type of computer network device that provides interconnection with other bridge networks that use the same protocol.
Bridge devices work at the data link layer of the Open System Interconnect (OSI) model, connecting two different networks together and providing communication between them. Bridges are similar to repeaters and hubs in that they broadcast data to every node. However, bridges maintain the media access control (MAC) address table as soon as they discover new segments, so subsequent transmissions are sent to only to the desired recipient.
Gateways:
A gateway, as the name suggests, is a passage to connect two networks together that may work upon different networking models. They basically work as the messenger agents that take data from one system, interpret it, and transfer it to another system. Gateways are also called protocol converters and can operate at any network layer. Gateways are generally more complex than switch or router.
d.
Sol:
Advantages of email :
(i). Low cost : Electronic mail is an extremely cost effective way to move information around. Especially when it must be moved quickly.
(ii). Speed : Electronic mail can be delivered at a very fast rate. We click and its gets sent.
(iii). Waste reduction : Email goes a long way toward reducing the cost of paper and per in modern office and thus saving lot of trees.
e.
Sol:
(a) Total cable length required for this layout = 75 mts
(b) To give dedicated bandwidth, the computers in each building should be
connected via switches as switches offer dedicated bandwidths.
(c) By installing routers in each building, shared internet access can be made
Possible.
(d) (i) Satellite as it can connect offices across globe.
(ii) WAN (Wide Area Network)
SECTION-C
Q.5.
a.
Sol:
Djangois a free and open source web application framework, written in python. Django is named after Django Reinhardt, one of the best jazz guitarist of all time. Django was mainly developed to handle the intensive design of the newsroom. We can build high quanlity web appliations using Django. It follows DRY() principle and focuses on automating as much as possible.
Advantages:
* Object Relational Mapping(ORM) Support: Django provides a bridge between the data model and the database engine and supports a large set of database systems including MYSQL, Oracle, Portgres etc.
* Supports No-SQL databse
* Multilingual supports: it supports multiples languages.
* Framework Support: Django has built-in support for Ajax and various other framworks.
* Administration GUI : Django provides a nice ready to use user interface for Adminstrator.
* Loosely coupled: Django aims to make each element of its stack independent of each other.
* Easy to extend and scale: Django has been evolving consistently to enable programmers to build better and modern web applications. At the same time, the Django developers can easily customize, scale, and extend the web framework by making changes to its decoupled components.
* less coding: Django requires less coding , so it can be developed rapidly.
b.
Sol:
Django can be broken into several components like:
* Models.py file : this file defines our data model by extending our single code line into full database tables and adds a pre-built administration section to manage content.
* urls.py file: this file consist of all the urls used.
* views.py file : it is the main part of Django. The actual processing happens in views.
c.
sol:
#display all the records from a table employee(empno,name,sal)
import pymysql
#Open database connection
conn=pymysql.connect(host='localhost',user='root',password='',db='databasename')
db = pymysql.connect("localhost","root","","employee")
#prepare a cursor object using cursor() method
try:
c = db.cursor()
sql='select * from employee;'
c.execute(sql)
countrow=c.execute(sql)
print("number of rows : ",countrow)
#data=a.fetchone()
data=c.fetchall()
#print(data)
print("Emp No Name Salary")
for eachrow in data:
e=eachrow[0]
n=eachrow[1]
s=eachrow[2]
# Now print fetched result
print(e," ",n," ",s)
except:
pass
#disconnect from server
db.close()
Q6.
a.
Sol:
Group by:
The group by clause can be used in a select statement to collect data from multiple records and group the results by one or more columns. It groups the rows on the basis pf the values present in one of the columns and then the aggregate functions can be applied on any columns.
Syntax:
Select col1,function(exp) from tablename group by col1;
Having :
The having clause helps us to apply condition with group by clause
Example:
Select pno,sum(qty) from product where pno=’p1’ or pno=’p2’;
b.
Sol:
(i) To display details of all the items in the store table in ascending order of Lastbuy.
Sol:
Select* from store order by lastbuy;
(ii) To display itemno and item name of those items from store table whose rate is more than 15.
Sol:
select itemno. Item from stor where rate>15;
(iii). To display the details of those items whose supplier code is 22 or quantity in store ( (Qty) is more than 110 from the table STORE.
Sol:
Select * from store where scode=22 or qty >110;
(iv) To display Minimum Rate of items for each Supplier individually as per Scode from the t able STORE.
Sol:
Select Scode, Min(Rate) from store Group by Scode;
Give the ouput of the following sql series:
(v) Select count(distinct Scode) From store;
Sol: 3
(vi) Select Rate*Qty from Store where ItemNo=2004;
Sol: 880
Q.7.
a.
Sol:
Open data is the idea that some data should be freely available to everyone to use and republish as they wish without restrictions of copyright, patent or other controls.
b.
Sol:
A few stpes to follow in order to prevent identity thefts:
* Ensure a strong password
* Avoid posting confidential information online
* Use latest version of browser
* Always update you system and the softwares.
* protect you aadhar card number
* download only well known apps and share limited details
c.
Sol:
Definition of ‘Cyber Security’
Definition: Cyber security or information technology security are the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation.
Description: Major areas covered in cyber security are:
1) Application Security
2) Information Security
3) Disaster recovery
4) Network Security
Application security encompasses measures or counter-measures that are taken during the development life-cycle to protect applications from threats that can come through flaws in the application design, development, deployment, upgrade or maintenance. Some basic techniques used for application security are: a) Input parameter validation, b) User/Role Authentication & Authorization, c) Session management, parameter manipulation & exception management, and d) Auditing and logging.
Information security protects information from unauthorized access to avoid identity theft and to protect privacy. Major techniques used to cover this are: a) Identification, authentication & authorization of user, b) Cryptography.
Disaster recovery planning is a process that includes performing risk assessment, establishing priorities, developing recovery strategies in case of a disaster. Any business should have a concrete plan for disaster recovery to resume normal business operations as quickly as possible after a disaster.
Network security includes activities to protect the usability, reliability, integrity and safety of the network. Effective network security targets a variety of threats and stops them from entering or spreading on the network. Network security components include: a) Anti-virus and anti-spyware, b) Firewall, to block unauthorized access to your network, c) Intrusion prevention systems (IPS), to identify fast-spreading threats, such as zero-day or zero-hour attacks, and d) Virtual Private Networks (VPNs), to provide secure remote access.
d.
Sol:
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, the freezing of the system as part of a ransomware attack or the revealing of sensitive information.
An attack can have devastating results. For individuals, this includes unauthorized purchases, the stealing of funds, or identify theft.
An organization succumbing to such an attack typically sustains severe financial losses in addition to declining market share, reputation, and consumer trust. Depending on scope, a phishing attempt might escalate into a security incident from which a business will have a difficult time recovering.
e.
Sol:
The network security components that we should have are:
• anit-virus and anti-spyware
• Firewall , to block unauthorised access to your network.
• IPS (Intrusion prevention system) to identify the fast spreading threats.
By Rajesh Shukla
Sample Paper 1 Solution Sample Paper 1
Sample Paper 2 Solution Sample Paper 2
CBSE Class 12 @ Python
Tutorials | Technical Questions | Interview Questions |
|---|---|---|
|
C Programming C++ Programming Class 11 (Python) Class 12 (Python) |
C Language C++ Programming Python |
C Interview Questions C++ Interview Questions C Programs C++ Programs |




